Find how to control your network
Learn more about our network management software products for network monitoring and network security to take control over your network simply and easily.
Products
Our Products
Products List
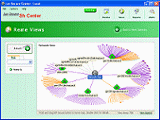
Switch Center - Network Management Monitoring Software
Switch Center is network management software for network monitoring of managed switches, routers and hubs from any vendor supporting SNMP BRIDGE-MIB that helps to discover, mapping and analyze networks topology and performance.
Switch Center can be connected through any network port without the need of remote agents or special network management configuration. The unique network monitoring engine provides complete network topology and performance of local and remote network nodes and interconnecting devices trunks. The software monitoring options support SNMPv1/2 and SNMPv3 discovery options including VLANs monitoring engine. The built-in central viewer supports multiple management levels and provides automatic network monitoring and mapping using OSI Layer 2 and Layer 3 topology. The software management capabilities include real-time reports, statistics and alerts.
- Real-time network management and monitoring.
- Nodes and users discovery including port location.
- Reports and statistics including exporting capabilities.
- Multi vendors network devices ports mapper and scanner.
- Network mapping, topology and performance supporting graphical views.
- Database exporting capability supporting SQL and HTML for online updating.
- Central viewer supporting multiple levels of management access permissions.
- Optional VLANs discovery and monitoring including optional views.
- Support SNMPv1/2 and SNMPv3 discovery.
- Email and SNMP trap alerts forwarding.
- Daily and weekly e-mail reports.
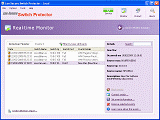
Switch Protector - NAC Network Access Control Monitor
Switch Protector is add-on engine of Switch Center software that provides Network Access Control (NAC) features on any managed network switches and hubs from any vendor supporting SNMP BRIDGE-MIB and helps to protect networks from potential intruders, unauthorized connections and malicious activities.
Switch Protector Network Access Control (NAC) software engine implements IEEE-802.1X features without the need for any special considerations for network switches or workstations. The software powerful engine provides real-rime intrusion detection and prevention based on selectable proven protection techniques including network nodes properties, activity and installed components. The software protection methods and rules can enforce any network security policy and can be implemented on all network switches or on specific selectable switches. The built-in central viewer supports multiple management levels including E-mail alerts, SNMP traps and SYSLOG notifications that provides maximum administration control and management capabilities.
- Network access control (NAC) software using online detection and SNMP traps.
- Network access detection of new MAC addresses and switch ports location changes.
- Network access protection against spoofing addresses that access as authorized nodes.
- Network access security for organization policy enforcement on end-users workstations.
- Network policy enforcement using linkup WMI properties and external remote scripts.
- Network access prevention using SNMP or any other script like Telnet or SSH.
- Network access control management using standard intranet web interface.
- Email messages, SNMP traps and SYSLOG notifications alerts.
- Online administration with email access control protection.
- Daily and weekly e-mail reports.
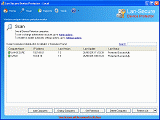
Device Protector - DLP Endpoint Device Control Security Software
Device Protector is Data Loss Prevention (DLP) and endpoint device control security software that enforce device protection policies on organization computers. The software helps to secure IT environments from un-trusted endpoint devices and prevent data leakage and information theft.
Device Protector can be deployed through the software management console or through any 3rd party deployment system by using the software deployment MSI package. The software provides online and offline protection including read-only, read-write, and working hours options. It can also provides exclude users and exclude media serial numbers capabilities. The software support all Windows operating systems and can protect the following devices: Bluetooth, DVD/CD-ROM, Firewire, Floppy, Imaging, Infrared, Microphones, Modems, Portable Mobile Phones, Ports, Printers, Removable Disks, Sound, Tape Drives and Wireless network devices.
- Provides Data Loss Prevention (DLP) device control endpoint security.
- Support endpoint device control for DVD/CD-ROM, Flash Drives, Mobile Phones, Wireless devices and more.
- Support online and offline endpoint security including read-write, read-only and working hours protection.
- Support device control exclude options of users and DVD/CD, Flash drives media serial numbers.
- Support multiple or redundant servers including first available or first responsive options.
- Support automatic discovery and deployment of network computers.
- Support remote control administration console with permissions.
- Support automatic DHCP release of protected wireless devices.
- Support client protection service unstoppable mode option.
- Support automatic actions and exporting capabilities.
- Support enhanced statistics and reports.
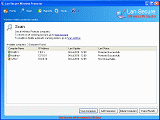
Wireless Protector - Auto Disable Wireless when LAN connected
Wireless Protector is automatically disable wireless when LAN/Ethernet is detected on computers that connected to the network with wired cable and re-enable the protected devices on disconnect. The software wireless auto switching capability helps to secure IT environments from un-trusted connections and prevent computers from using duplicate network resources.
Wireless Protector is acting as a server to all protected computers and can be deployed through the software management console or through any 3rd party deployment system by using the software deployment MSI/OSX installation package. The software powerful engine can secure any number of computers by installing a remote service on the protected computers. It provides easy-to-use network administration interface including auto discovery, auto scanning, reports, actions, exporting capabilities, database support and remote administration console. The software support Windows or Mac-OSX operating systems and can protect the following devices: Bluetooth, Firewire, Infrared, Modems, Portable Wireless Phones, Removable USB and Wireless 802.11 and Broadband (3G / 4G / WiMax) network devices.
- Disable wireless when wired or docked.
- Disable wireless when on lan or lan connected.
- Disable wifi or wlan when lan connected or wired.
- Disable wireless when ethernet is detected or connected.
- Real-time wireless auto switch between wlan and ethernet.
- Prevent computers from using duplicate network resources.
- Prevent from exploit wireless and endpoint devices as network bridge.
- Automatically disable wireless on Mac-OS X operating systems.
- Automatically disable wireless on Windows XP, Vista, 7, 8, 10.
- Support protection service with unstoppable mode option.
- Support automatic actions and exporting capabilities.
- Support enhanced statistics and reports.
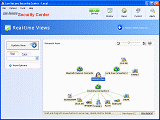
Security Center - Network Management Protection Software
Security Center is network management software for network security that implements real-time intrusion detection IDS and prevention IPS and helps to protect networks from potential intruders, unauthorized connections and malicious activities.
Security Center can be connected in any network either it is switched or hubs network without the need of remote agents or special network management configuration. The unique network monitoring engine provide real-time threats and vulnerabilities discovery. The built-in manual and automatic network monitoring protection rules enable to enforce any network security policy with proactive blocking of network nodes that violated the security protection rules. The software can be used in distributed environment using any number of remote network management viewers for controlling the network security permissions and operation status. The built-in central software management viewer support local and remote sites including online reports and alerts.
- Provides online network security and protection monitoring.
- Automatic network monitoring of threats and vulnerabilities level.
- Network access protection using organization policy enforcement.
- Real-time manual and automatic access protection rules against potential intruders.
- Real-time access protection using intrusion detection IDS and prevention IPS services.
- Real-time nodes display for analyzing network connections and transmission rates.
- Real-time access protection using MAC, IP, DNS name or Username attributes.
- Proactive network access protection using threat and vulnerability levels.
- Alerts forwarding using SMTP, SNMP, SYSLOG and Commands.
- Support wireless intrusion detection and prevention.
- Daily and weekly e-mail reports.
Burn Protector - Secure Burning Management Software
Burn Protector is CD/DVD/Blu-ray burning security management software that implements burn permissions on protected computers. The software helps to secure IT environments from burning sensitive data and prevent organization information theft.
Burn Protector can be installed through the software management console or through any 3rd party deployment system by using the software deployment MSI package. The software enables read-only access to the protected computers burning devices through its own secured burning interface. Its powerful engine can protect any number of computers and monitor the protected computers for active burning permissions. The software provides easy-to-use network administration interface including auto discovery, auto scanning, reports, actions, exporting capabilities and database support. The software also collects burning events and configuration changes that help network administrators to track and maintain the protected computers.
- Provide secure burning management of CD/DVD/Blu-Ray.
- Implements burning access permissions to users and folders.
- Secure organization sensitive data from confidential information theft.
- Support automatic active protection discovery and scanning of protected computers.
- Support multiple redundant servers including first available or first responsive options.
- Support client protection service unstoppable mode option.
- Support enabling and disabling clients multisession option.
- Support enabling and disabling clients burning size limit.
- Support automatic actions and exporting capabilities.
- Support remote control administration permissions.
- Support enhanced statistics and reports.
Documents Protector - Document Security Management Software
Documents Protector is document security management software that implements discovery, alerting and blocking of documents that includes protected words and phrases. The software helps to secure IT environments from writing confidential and sensitive data to documents and prevent organization information theft.
Documents Protector can be installed through the software management console or through any 3rd party deployment system by using the software deployment MSI package. The software is tracking write operations in selected folders on the protected computers and search for the selected restricted words and phrases. Its powerful engine can protect any number of computers and monitor the protected computers for active documents protection. The software provides easy-to-use network administration interface including auto discovery, auto scanning, reports, actions, exporting capabilities and database support. The software also collects documents protection events and configuration changes that help network administrators to track the protected computers.
- Provide document security using restricted words and phrases.
- Implements document security protection to selected folders and phrases.
- Secure organization confidential and sensitive documents from information theft.
- Support automatic active protection discovery and scanning of protected computers.
- Support multiple redundant servers including first available or first responsive options.
- Support multiple document formats including PDF, Word, Excel, Power Point, compressed and textual.
- Support protected documents quarantine folder and client notification message.
- Support client protection service unstoppable mode option.
- Support automatic actions and exporting capabilities.
- Support remote control administration permissions.
- Support enhanced statistics and reports.
Inventory Center - Windows Asset Management Software
Inventory Center is real-time windows inventory asset management software that using WMI service for monitoring servers and workstations operating systems. The software provides automatic monitoring, reports, actions and exporting capabilities.
Inventory Center software can be operated on any network environment without the need of remote agents or special network configuration. It is using the already installed WMI (Windows Management Instrumentation) service to explore operating systems of windows servers and workstation. The monitoring inventory asset includes Computer, System, Devices, Programs, Processes, Services, Updates, Exchange and IIS server properties and open ports scanning. The software powerful monitoring engine can support any number of windows servers and workstations and provides real-time monitoring, reports and actions like rebooting and processes and services control options. The software is also providing custom actions like command execution, email forwarding and syslog notifications as well as database exporting capabilities.
- Provides real-time windows inventory asset management.
- Enables selectable windows inventory asset information properties.
- Enables automatic startup and monitoring options of windows computers inventory asset.
- Enables automatic actions including e-mail, command execution and syslog notification events.
- Enables automatic exporting capabilities to text file or any SQL/Access ODBC databases.
- Provides enhanced statistics and reports including selectable user-define report.
- Provides real-time monitoring of windows properties with optional actions.
- Provides real-time monitoring of Exchange, IIS and SQL servers.
- Provides real-time active TCP ports scanning.
- Support enhanced statistics and reports.
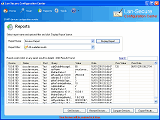
Configuration Center - Network Configuration Management Software
Configuration Center is real-time windows based network configuration management software for Telnet SSH and SNMP devices from any vendor that backup configurations, monitor history changes, compare changes and restore configurations of network devices.
Configuration Center software is designed to save time and reduce configuration errors in distributed administration environment by monitoring and collecting devices configuration from any network location. The software monitoring engine can be operated manually by user request or run automatically on specific dates and times. The software can provides dynamic actions like executing commands or sending specific SNMP trap or email on specific configuration changes. It can also provides reporting, logging and exporting capabilities that can be used for enhanced management of current and historical network devices configuration.
- Provides real-time network configuration management.
- Support configuration monitoring of manageable devices from any vendor.
- Support Telnet SSH and SNMP version 1/2/3 network devices configuration.
- Enables automatic actions capabilities such as e-mail, SNMP traps and command execution.
- Enables automatic exporting capabilities to text file or SQL/Access ODBC databases.
- Provides enhanced statistics and reports including L2 and L3 interfaces options.
- Provides automatic configuration backup on specific dates and times.
- Provides historical network configuration management capabilities.
- Provides configuration changes on any number of devices.
- Provides network configuration comparison.
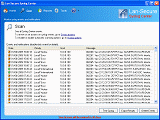
Syslog Center - Network SYSLOG Management Software
Syslog Center is real-time network management and monitoring server daemon for syslog events that collects messages and notifications from any network device and helps to monitor, analyze and correlate network events in IT environments.
Syslog Center implements syslog server monitoring daemon. The powerful software monitoring engine can analyze any number of syslog events in real-time and perform special actions and correlation reports upon receiving specific network messages and events. The software can also be used as central monitoring engine with exporting capabilities such as database and textual log files that can provide online and historical repository for network administrators. The software built-in viewer can provide advanced syslog reports including root cause analysis that can in used in heavy loaded IT environments.
- Provides real-time Windows and Mac syslog server daemon.
- Provides real-time monitoring of syslog events with optional actions.
- Enables advanced filtering based on host address, priority and message text.
- Enables automatic actions including e-mail, command execution and event log.
- Enables automatic exporting capabilities to text file or SQL database.
- Provides enhanced statistics and reports including events correlation.
- Provides real-time events correlation for root cause analysis.
- Provides automatic events management capabilities.
- Provides automatic popup alerts.
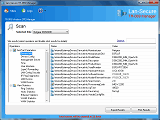
TR-069 Manager - Windows ACS for CWMP management
TR-069 Manager is real-time windows based software for CWMP management that provides ACS capabilities to manage remote CPE sites and helps to get and set parameters, view statistics and perform actions on any TR-069 supported devices.
TR-069 Manager software is providing intuitive user interface that provides collection of TR-069 categories to support any CPE device. The software CWMP management engine support any number of remote CPE sites with different ACS capabilities that includes parameters, statistics and actions with connection and operation logs. The CPE and ACS settings of the software includes port numbers selection with optional username, password and proxy settings that support any type of remote connections.
- Provides real-time TR-069 ACS capabilities.
- Provides windows based CWMP management capabilities.
- Enables get and set parameters of any remote CPE devices.
- Enables statistics and actions on remote managed CPE devices.
- Enables selectable CPE and ACS settings with optional username, password and proxy.
- Enables TR-069 user specific parameters requests.
- Provides last connection and operation logs.
- Provides intuitive user interface.
- Enables TR-069 exporting results.
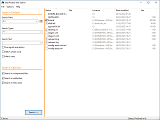
Win Search - text searching in standard and compressed files
Win Search is windows based software for text searching in standard or compressed files and folders. It provides real-time text searching capabilities for finding text or phrases in standard and any type of compressed files and folders. The software also provides text matching capabilities like regular expressions, whole word and case matching.
Win Search software is providing standard and compressed text searching that using a safe memory sandbox for opening compressed files without writing any data to the local disks and that way preventing from any malware or computer virus to effect the searched computer. It is also using intuitive user interface that provides collection of text searching capabilities and optional compressed files passwords list and files and folders exclusions.
- Provides real-time windows text searching capabilities.
- Provides text searching for windows based standard and compressed files.
- Enables text searching capabilities including regular expressions, whole word and match case.
- Enables text preferences including speed, statistics, exclusions and compressed files passwords.
- Enables text searching options including compressed files, subfolders and filenames.
- Enables search statistics including time, scanned files and folders and status result.
- Enables text searching optimization for any specific user needs.
- Provides search statistics results.
- Provides intuitive user interface.
