Lan-Secure Device Protector
Endpoint device control and Data Loss Prevention (DLP) security software for Windows providing enforcement of device control protection policies.
Device Protector
DLP Endpoint Security Management

Device Protector is Data Loss Prevention (DLP) and device control endpoint security software that enforce endpoint devices protection policies on organization computers. The software helps to secure IT environments from un-trusted endpoint devices that can be used by potential intruders to access sensitive organization data and prevent data leakage and information theft.
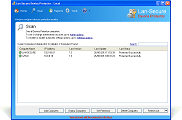
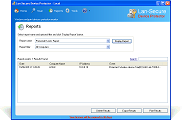
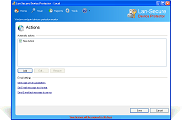
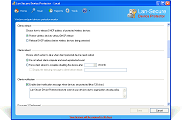
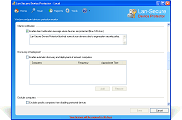
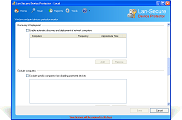
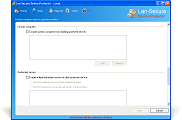
Device Protector is acting as a server to all protected computers and can be deployed through the software management console or through any 3rd party deployment system by using the software deployment MSI package. The software powerful engine can control and secure any number of computers by installing a remote service on the protected computers. It is supporting devices online and offline protection including read-only, read-write, working hours, exclude users and exclude media serial numbers capabilities. It is also providing easy-to-use network administration including auto discovery, auto scanning, reports, actions, exporting capabilities, database support and remote administration console. The software can collect activity logging with optional actions on the protected endpoint devices that helps network administrators to track and maintain the organization endpoint security and data loss prevention.