Network Management and Monitoring Software
Network management software for network monitoring of managed switches and hubs from any vendor supporting SNMP BRIDGE-MIB that helps to discover, mapping and analyze networks topology and performance.

- Real-time network access detection and prevention monitoring.
- Network access detection using online discovery and SNMP traps.
- Organization policy enforcement rules on end users workstations.
- Can manage all network segments from single location.
- Reports and statistics including exporting capabilities.
- Support SNMPv1/2 and SNMPv3 discovery.
- No need for remote agents.
Network Access Control Software
Network Access Control (NAC) software that implements IEEE-802.1X protocol features on SNMP enabled network switch ports and helps to protect networks from potential intruders, unauthorized connections and malicious activities.
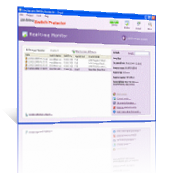
- Real-time network access detection and prevention monitoring.
- Network access detection using online discovery and SNMP traps.
- Organization policy enforcement rules on end users workstations.
- Can manage all network segments from single location.
- Reports and statistics including exporting capabilities.
- Support SNMPv1/2 and SNMPv3 discovery.
- No need for remote agents.
DLP Endpoint Device Control Security Software
Data Loss Prevention (DLP) and endpoint device control security software that enforce endpoint devices protection policies and helps to secure IT environments from un-trusted endpoint devices that can be exploit for data information theft.
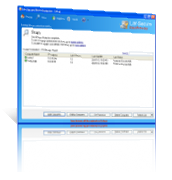
- Real-time Data Loss Prevention (DLP) device control endpoint security.
- Support DVD/CD-ROM, Flash Drives, Mobile Phones, Wireless devices and more.
- Online and offline endpoint security with read-write and working hours options.
- Device control exclude options of users and media serial numbers.
- Automatic discovery and deployment of network computers.
- Reports and statistics including exporting capabilities.
- Client protection service unstoppable mode option.
Disable Wireless When Connected to LAN
Automatically disable wireless when LAN/Ethernet is detected on computers that connected to wired network and re-enable them on disconnect. It helps to secure networks from un-trusted connections and duplicate network resources.
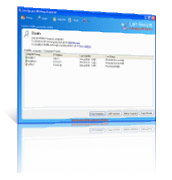
- Real-time wireless auto switch and endpoint security.
- Prevent computers from using duplicate network resources.
- Prevent from exploit wireless and endpoint devices as network bridge.
- Activity logging and reports on protected computers.
- Acting as a server to all protected computers.
- Built-in and self deployment clients options.
- Support Windows and Mac-OSX platforms.
Network Security and IDS/IPS Software
Network security and protection software that implements real-time intrusion detection IDS and prevention IPS and helps to protect networks from potential intruders, unauthorized connections and malicious activities.
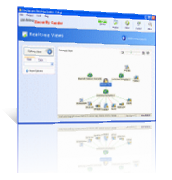
- Real-time network access detection and prevention.
- Graphical views of network mapping, activity and protection.
- Automatic network discovery and real-time security analizing.
- Can be connected and protect any network segment.
- Reports and statistics with exporting capabilities.
- Support organization policy enforcement rules.
- No need for remote agents.
Secure Burning Management Software
Secure burn management software that implements burning permissions on computers files, folders and users. It helps to secure IT environments from burning sensitive data and prevent organization information theft.
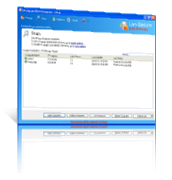
- Real-time secure burning management of CD/DVD/Blu-ray.
- Prevent execution of files on protected computers burning devices.
- Implements burning access permissions to users and folders.
- Acting as a server to all protected computers.
- Unstoppable client protection service option.
- Built-in and self deployment client options.
- Support multiple redundant servers.
Document Security Management Software
Document security software that implements real-time management of protected words and phrases. It helps to secure IT environments from writing confidential and sensitive data to documents and prevent organization information theft.
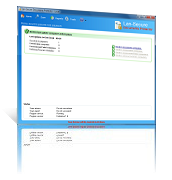
- Real-time document security management of restricted words and phrases.
- Provide document security protection on selected folders and phrases.
- Support optional client notification message for blocked documents.
- Support optional quarantine folder for blocked documents.
- Acting as a server to all protected computers.
- Unstoppable client protection service option.
- Support multiple redundant servers.
Windows Inventory Asset Management Software
Windows asset management software using WMI service for monitoring servers and workstations operating system inventory that provides real-time scanning, reports, actions and alerts.
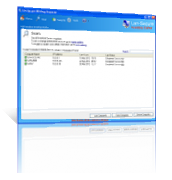
- Real-time windows inventory asset management.
- Selectable windows inventory asset information properties.
- Enhanced statistics and reports including selectable user-define report.
- Real-time monitoring of windows properties with optional actions
- Real-time monitoring of Exchange and IIS servers properties.
- Real-time active TCP ports scanning.
- No need for remote agents.
Network Configuration Management Software
Network configuration management software for Telnet SSH and SNMP devices from any vendor that helps to backup configurations, monitor history changes, compare changes and restore configurations of network devices.
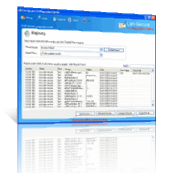
- Real-time configuration management of devices from any vendor.
- Support Telnet/SSH shell protocols and SNMPv1/2/3 protocols.
- Automatic configuration backups on selected dates and times.
- Automatic actions on discovery of specific configuration.
- Reports and statistics with exporting capabilities.
- Support multiple devices configuration changes.
- Support restore and comparison capabilities.
Syslog Server Monitoring Software
Syslog server monitoring software for syslog events that collects messages and notification alerts from any device or vendor and helps to monitor, analyze, report and correlate real-time network events in IT environments.
- Real-time monitoring and viewing of syslog events.
- Automatic actions upon receiving specific syslog events.
- Automatic filtering options of specific syslog events.
- Correlation reports including exporting capabilities.
- Support syslog notifications to log events options.
- Support exporting capabilities to text or database.
- Support popup and sound notifications.
TR-069 Windows ACS for CWMP management
Windows based software for CWMP management that provides real-time ACS capabilities to manage remote CPE and helps to get and set parameters, view statistics and perform actions on any TR-069 supported devices.
- Provides real-time TR-069 ACS capabilities.
- Provides windows based CWMP management.
- Enables get and set parameters of any remote CPE sites.
- Enables statistics and actions on remote managed CPE sites.
- Enables selectable CPE and ACS settings with optional proxy.
- Provides last connection and operation logs.
- Enables TR-069 exporting results.
News
News & updates
News List
Move mouse over an item for reading
SC Magazine, a popular IT security magazine has reviewed and awarded Lan-Secure Security Center with their top most "Best Buy" award in Policy management group test for 2006.
Switch Center - 3D2F.com "Best among the like" awardEditors team at 3D2F.com, a leading software directory for freeware, shareware, demo and commercial software, has reviewed and awarded Lan-Secure Switch Center as "Best among the like", saying that it is "the most promising in its class".
Network Tools - Windows network scripts libraryNet scripter is easy to use software DLL (Dynamic-Link Library) that helps to create network management scripts and supports Ping, Snmp, Telnet and Textual Encoding (B64 and TEA).
Network Tools - Windows Syslog monitor server daemonLan-Secure Windows Syslog Monitor is a real-time network management and monitoring server daemon for syslog events that collects messages and notification alerts from any vendor and helps to monitor, analyze, report and correlate events in IT environments.
Network Tools - SNMP Network Configuration ManagementLan-Secure Configuration Center is network configuration management software that monitors changes of Telnet SSH and SNMP network devices configuration from any vendor and provides setting, changing, collecting and restoring configuration of network devices.
Network Tools - Auto disable wireless when connected to lanLan-Secure Wireless Protector implements auto switch between WiFi and LAN connections on Windows / Mac-OSX wireless computers that helps to secure networks from un-trusted WiFi connections that can be used by potential intruders as a network bridge and also prevent computers from using duplicate network resources.
Win Search - text searching in standard and compressed filesWindows based software for text searching in standard and compressed files and folders that provides real-time text searching capabilities.
Outlook Notifier - free desktop/logon outlook unread mailLan-Secure Free outlook unread mail gadget-like software including desktop and logon screen display with constant and popup viewing modes.
